Overview of the four challenges
© Plattform Industrie 4.0
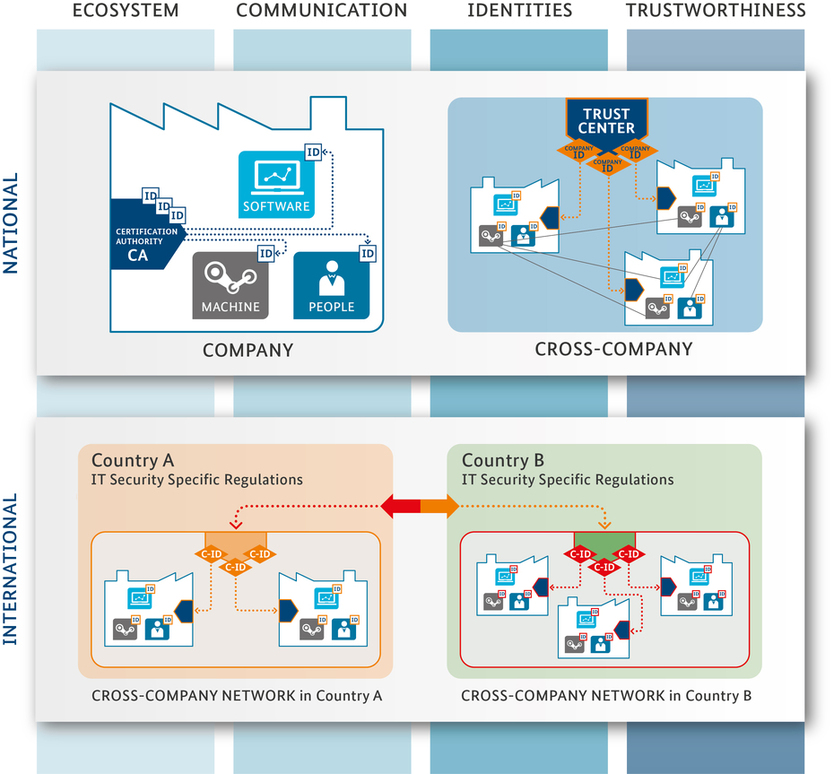
Secure eco-system
Overview eco-systems
© Plattform Industrie 4.0
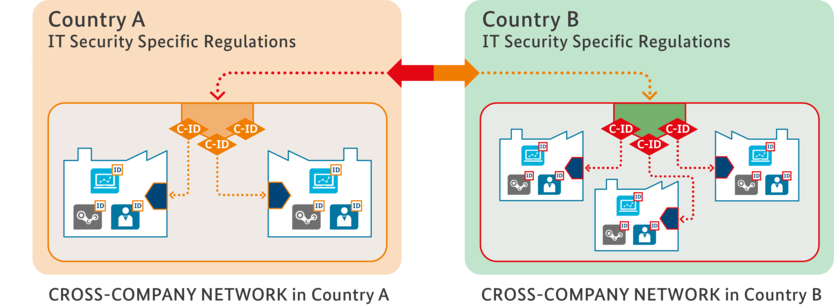
Global value networks require comprehensive security architectures that provide protection to all participants, regardless of which country they are located in. The integrity of processes, machines and products must be ensured throughout the entire production process. To manage this feat and to work successfully together across borders, we need a generally accepted approach to security, interoperable security strategies and a common regulatory framework.
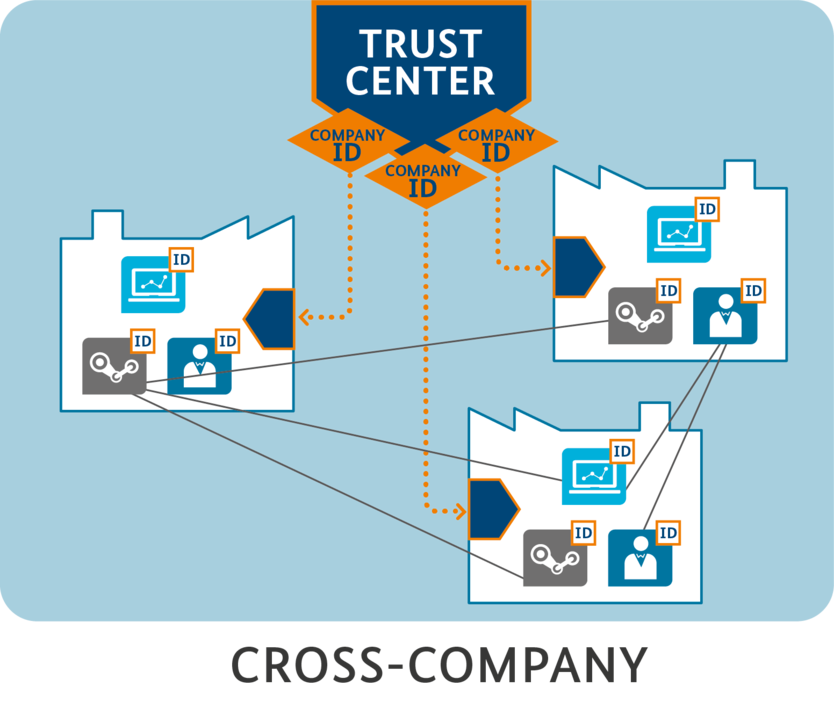
One step towards safer ecosystems is security-by-design. Security measures can be integrated into industrial applications and support end-to-end security solutions. The same should apply to the digital model: security for physical systems, their digital twin and their respective interactions must take place in a coordinated framework. Certification bodies or "trust centers" are necessary for secure cross-border data transfer between machines. The “trust centers” act as trusted neutral entities and issue certificates in security domains. Assigning or cancelling rights must be granted by the respective domain. For this to work outside of national borders, “trust centers” must enter into agreements with each other, creating conditions for secure communication that meets national requirements. There are no examples so far. A possible concept and/or implementation could entail identity management and roaming contracts provided by mobile operators.
Secure communication
Overview secure communication
© Plattform Industrie 4.0
Secure cross-company communication in international value networks must take into account and synchronize the security needs of all stakeholders. Securely exchanging data across enterprises and across borders requires interoperable security strategies and transparent identity mapping.
Authenticity, integrity and trustworthiness of the communication partners can be checked. Both the confidentiality of the information and the verification of the communication must be taken into account.
| Publication: Technical Overview: Secure cross company communication |
Secure identities
Overview secure identities
© Plattform Industrie 4.0
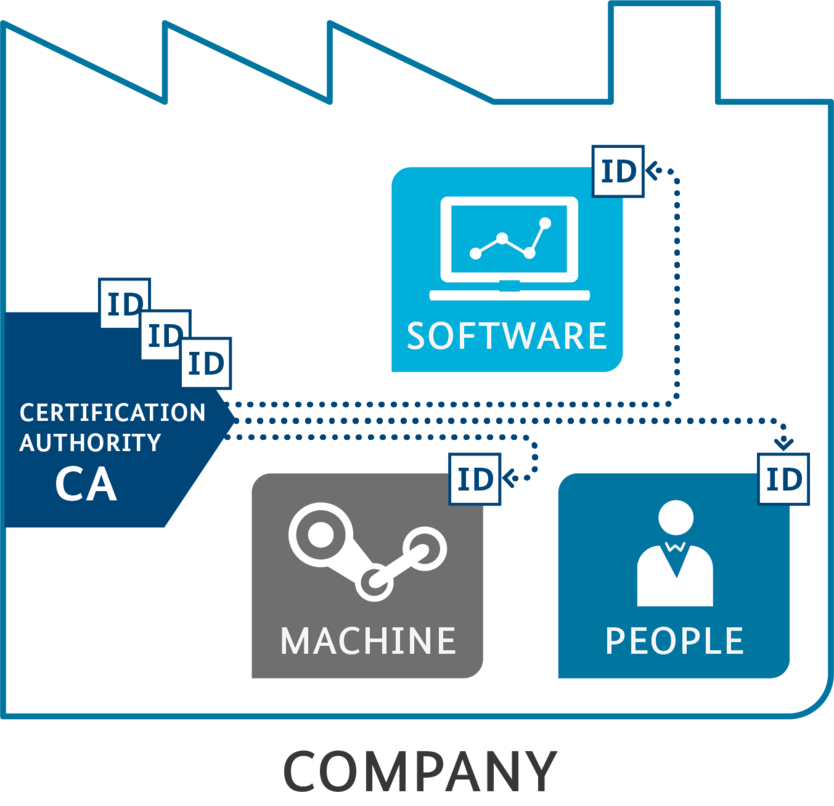
When humans, machines and software communicate with each other, they need to know who they are talking to. In the Industry 4.0 context, assets must be equipped with secure identities. Within a corporation, a certification authority or "Certification Authority" (CA) can provide these secure identities.
A trusted certification authority, as a security manager, can can manage the identities of all instances of a security domain. In today’s world, a public key infrastructure (PKI) is a possible solution.
| Publication: Technical Overview: Secure Identities |
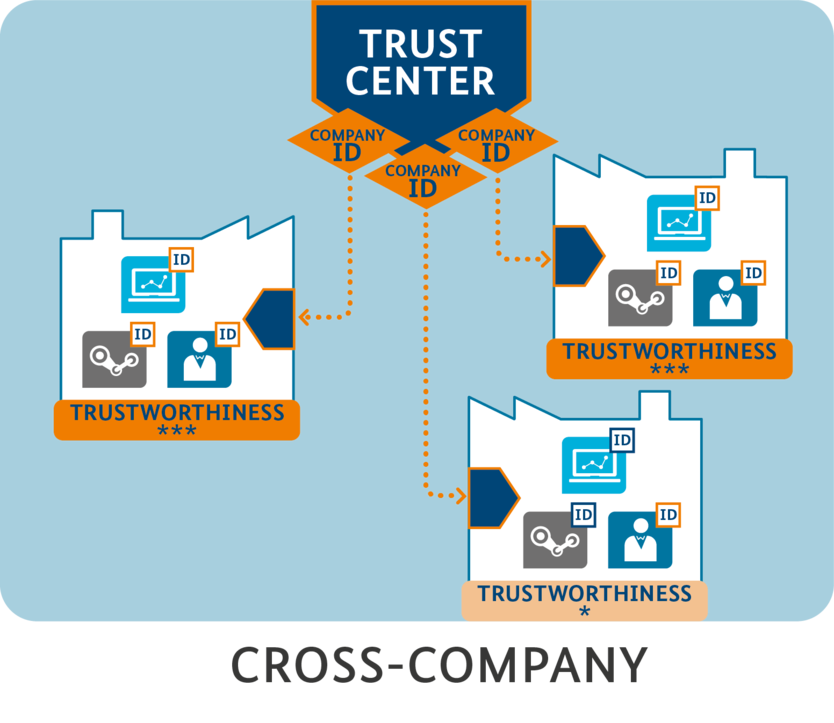
Trustworthiness
Overview trustworthiness
© Plattform Industrie 4.0
To ensure successful exchange of data, communication partners have to have trust in the communication infrastructure and the processing of the data. Apart from the technical components, the secure exchange of data also depends on partners having a well-integrated, reliable and verifiable security strategy. If cooperation with new partners begins, organisational and technical solutions should be set up to evaluate the degree of trustworthiness and, if necessary, to automatically transfer these to potential partners (comparable to intelligent scoring and rating on Amazon, etc.).
The term "trustworthiness" describes the nature of existing and future relationships between companies, people, systems and components. The five criteria of trustworthiness are: Security, Safety, Privacy, Reliability and Resilience. Integrity is an important core element of all five criteria of trustworthiness. Without integrity, the trustworthiness falters, as the probably action of a single unit cannot be determined. This concept applies to both "Operational Technology" (OT) and "Information Technology" (IT) – weighted differently between the five categories depending on the context.
| Publication: Integrity of data, systems and processes |



